Many Mac owners are probably not aware that there is an excellent way to store passwords in OS X. In this how to guide, we will tell you everything about why you should use this feature, and how you can start taking advantage of it today.
We have written about how to secure your data with Apple OS X before. But what about your passwords? You could put them in an encrypted file, but there is a certain amount of effort involved with this. Every time you want a password you have to unlock your encrypted disk, and open some text file.  Chances are you will tire of that, and then you’d be back to writing your passwords on little post it notes. Or even worse: you’ll start choosing passwords that are easy to remember. This is one of the cardinal mistakes when trying to live securely. Memorized passwords are usually the worst passwords; simple, easy to guess and likely to be reused. How many people are reading your email right now because you choose your high school sweetheart’s name as your password?
Chances are you will tire of that, and then you’d be back to writing your passwords on little post it notes. Or even worse: you’ll start choosing passwords that are easy to remember. This is one of the cardinal mistakes when trying to live securely. Memorized passwords are usually the worst passwords; simple, easy to guess and likely to be reused. How many people are reading your email right now because you choose your high school sweetheart’s name as your password?
There is a much better way to store passwords securely on the Mac:  Apple Keychain. The Keychain comes built in with your OS X operating system. If you are aware of it, you may think that its only function is to store your Safari and Apple Mail passwords. It can do much more than that.
Apple Keychain. The Keychain comes built in with your OS X operating system. If you are aware of it, you may think that its only function is to store your Safari and Apple Mail passwords. It can do much more than that.
Keychain encrypts all your passwords so that they can be stored securely, and yet the keychain is fast to use and organizes all your passwords to make them easy to find. Keychain is more secure than post-it notes, and much faster to access than a disorganized encrypted text file somewhere on your hard drive. Ultimately, Keychain can make your online experience much safer. You will be able to choose very tough passwords, and yet you will only need to memorize a single master password: your keychain password.
Here’s how to add any password for any account to your Keychain.
How to Add Any Password to the Keychain
- Open Apple Keychain. You can do this either by spotlighting for ‘keychain’, or by locating the ‘Access Keychain’ icon in your utilities folder.
 Hit Apple+N, or select ‘New Password Item’ from the File menu.
Hit Apple+N, or select ‘New Password Item’ from the File menu.
- Enter a good name for your password item. This will be the most important tag for finding your password item later, so make sure you pick something sensible. If the password is for a website, it’s often useful to put the address of the site in the name field.
- Enter your account name.
 Type in a password of your choice. You may click the key icon to the right of the Password field to open up Keychain’s built in password assistant.
Type in a password of your choice. You may click the key icon to the right of the Password field to open up Keychain’s built in password assistant.- If you need a copy of your password immediately, select ‘Show Typing’ to reveal your password.
Yep, it’s that easy. Here’s an example:
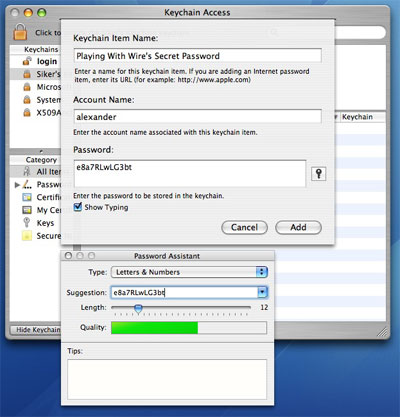
Now lets look at how to get the password back once you have stored it.
How to Get the Password You Need in Three Easy Steps
- Open Apple Keychain, by spotlighting for ‘keychain’ or by locating the ‘Access Keychain’ icon in your utilities folder.
- To search for a key, enter the Keychain Item Name or the Account name in the search box in the upper right corner of the program. When you can see your password in the list, just double click it.
- To see your password, check ‘Show Password.’ You will be asked for your keychain password. Unless you changed this master password, it will be the same as your login password.
Here’s the password we stored in our example:
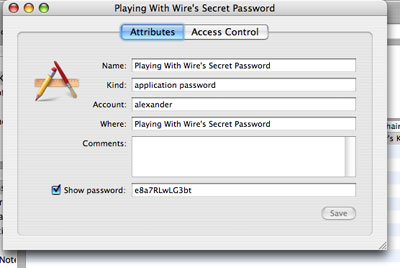
If you want to be able to access your passwords even faster, you can go into Keychain’s Preferences and check ‘Show Status in Menu Bar’. This adds a padlock in the Menu Bar. Clicking on the padlock reveals a menu that does not only allow you to reveal your keychain quickly, but also gives you a convenient ‘lock screen’ feature.
As you can see, getting to any one password is easy with Keychain. And even then, the passwords are protected and require your master password for display. You can have a unique password for every website you visit if you so wish, safe in the knowledge that if a password does come out, your other online activity will be unaffected.
Author: Alexander Ljungberg Tags: guide, Mac OS X






 Plug This!
Plug This!