Comments Off
Category:
Other
I know that we haven’t published anything in a couple of days, but we haven’t forgot about you guys. We think about you a lot. Yesterday Alex and I spent all day working (did you pay attention to that the Latte-counter increased by 6?), and while doing that we thought about topics for future articles. May we tease you a bit with topics such as building an intranet with LDAP-authentication or scripts for an (bandwidth efficient) uptime-monitor of an array of servers with mail-alert?
We also have a couple of cool Web 2.0-pages we want to share with you as well.
We promise we’ll take the time to publish a cool article within the next few days.
Author: Viktor Petersson Tags: WireLoad
For a quite a while I’ve been into the whole GTD movement. I must admit that I never got around to read the actual book which started the whole thing, but I have read a lot about GTD.
Until recently I used a GTD-plugin to OmniOutliner, which worked quite well. However, I was tired of having to have OmniOutliner running all the time, so I started looking for alternatives. Since we currently live in the ‘Web-based era,’ I looked around for some Web 2.0 GTD web-app. As it turns out, there’s a couple of them, but the one I really liked was Simple GTD. This software is a really clean Web 2.0-looking web-app with a simple user interface. First time you visit the site, you just create you user account, and you’re set. Now you can just start adding you items.
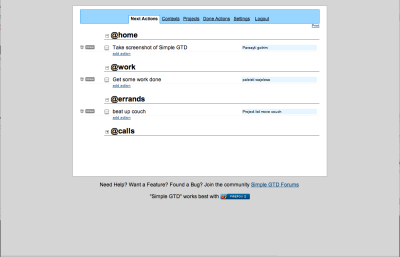
If you’re curious about how Simple GTD works, take a look a this screencast.
Author: Viktor Petersson Tags: guide
Comments Off
Category:
Other
As you might have noticed, the flow of articles has decreased here at PWW. No, we didn’t give up on you guys, we’re still thinking about you.
The reason for the lower flow is because both Alex and I are out traveling to visit family for the Christmas. We want to write more, but people tend to get upset when you travel around the world to see them, and end up sitting in front of the computer when you get there.
Even though we don’t get as much work done as we want, we still get some work done. Right now I’m sitting at a coffee-house in Gothenburg, Sweden, waiting for Alex to arrive so we can work together for a couple of hours.
Author: Viktor Petersson Tags: WireLoad
Comments Off
Category:
Other
In a recent writeup, BBC News covers a study by Lancaster University’s Professor Tony McEnery. It was also covered by Ars Technica, who put some attention grabbing spin on it by titling their article “Are iPods shrinking the British vocabulary?”
What the quoted study claims is that an excessive focus on technology is turning teenagers into passive listeners without ability to express themselves in spoken language.
Playing With Wire are today publishing an even more shocking study: both BBC News and Ars Technica are going down the same path as these teenagers. A word analysis of the BBC News article cited above reveals that a full 16% of the words in the article are common words such as ‘of’ and ‘in’.
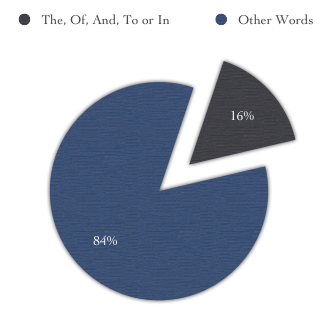
Break-down of the words used in the BBC article. The most common words are used 68 times in an article of only 419 words.
The Ars Technica article also fails to impress in the vocabulary department. 54 of the 301 words in the article are extremely common and simple words. Just like in the BBC News article, the word ‘of’ is used to express a large part of the content.
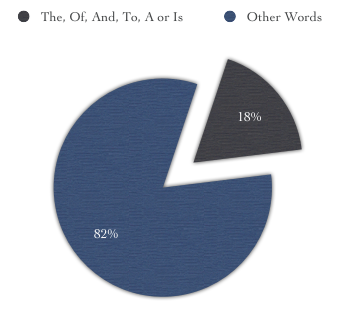
Break-down of the words used in the Ars Technica article. Very common words are used 54 times in this short 301 word article.
Our analysis here at Playing With Wire indicates that since both the Ars Technica and the BBC News articles are published online, there is an excessive reliance on technology. An almost machine like approach to creating articles results in this bleak lack of imaginative word usage.
We absolutely do not think unification of the English language occurs online to reach the widest possible audience. In fact this ubiquitous unsophisticated locution employment has us flabbergasted. It’s stupefying.
Author: Alexander Ljungberg Tags: analysis

This article is going to teach you how to get out the big guns against information theft on your Apple OS X machine. ‘But,’ you say, ‘I don’t have secrets and besides no-one cares about my stuff.’ Think again! If you are a normal computer user it doesn’t take long before you have plenty of very interesting information on your laptop, digitized and ready to be stolen in seconds.

My secret politically sensitive picture – out in the open and ready to be stolen.
- Your website passwords
- Those handy digital bank statements
- Your accounting information
- That picture from the office when you were really drunk
- Your other girlfriend’s or boyfriend’s phone number
Then think about how quickly someone can make a complete copy of all that data: it can take seconds or minutes. And what’s worse, once the cat is out of the bag, it’s likely you won’t manage to get it back in because it will be plastered over half of internet and stored in a database before you know it. We live in the beginning of the information age and information theft is real, fast, and internet enabled.
If you use Safari, most of your passwords are already protected within your Apple Keychain. This guide is about how to protect the rest of your stuff using encrypted disk images. An encrypted disk image is basically a protected folder which you can store on your computer. If you haven’t heard of it yet, encryption is a method to warp data so it can’t be recognized without doing the same process again backwards. In OS X 10.4, this encryption is not toy encryption either. The standard used, AES-128, is the encryption used for ‘SECRET’ level classified information of the American government.
It is all rather simple; just keep in mind that these tips have been written for OS X Tiger (version 10.4) and that things might be a bit different if you have a different version of OS X.
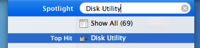 Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.
Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.- Click the ‘New Image’ button in the upper left part of the main window, or go to File>New>Blank Disk Image in the menus.
- Type in a nice name for your new disk image. I’m going to call mine ‘My Eyes Only’. I’m also going to make it 40MB big by selecting that from the size drop down.
- Set Encryption to ‘AES-128′. Don’t forget to do this or you’re not protecting your data at all!
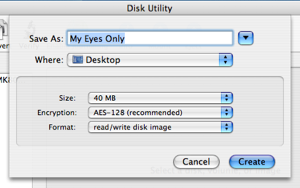
- Click create. You will be asked for a password. Make sure you enter something that you won’t forget, because else your data will be gone forever. No-one will be able to get your data out if the password is lost.
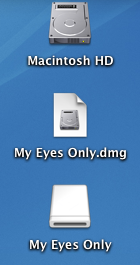 Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.
Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.- Once you are done putting files into your encrypted drive, you will need to eject it.
That’s all. Everything you put into your encrypted drive, ‘My Eyes Only’ in this example, will be encrypted with industry standard encryption. Without your password (which you made really sure to memorize and keep safe) it would take thousands of years for a modern day computer to unscramble your data. I’m just going to go ahead and move my Secret.JPG file into My Eyes Only. Here it is in the safety of 128 bit encryption: 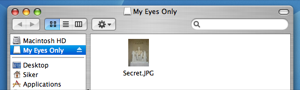
Once I eject this disk the data will be safe and I can rest assured that my picture is a little bit more safe from prying eyes.
Author: Alexander Ljungberg Tags: guide,
Mac OS X,
security










 My secret politically sensitive picture – out in the open and ready to be stolen.
My secret politically sensitive picture – out in the open and ready to be stolen.

 Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.
Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.