
We were well prepared. We had every possible company paperwork neatly filed in a manila folder, three forms of personal identification each; our suit pants had perfect creases, our shirts crisp white. When we entered the bank, heads turned.
Either that or we were dressed pretty much like normal and didn’t have a single form except in digital format. And when we entered the bank we had to sit down and wait like everyone else. :)
Either way we have now taken our first ‘official’ action as a company, and WireLoad has opened a bank account. The idea is mostly that we want to pay things out of a company account instead of our personal accounts going forward.
Just to let you know: Washington Mutual, the bank of our choice, was not able to accept digitalized copies of company documents. The following things were needed, at least here in California and for Washington Mutual:
- Articles of Organization, with the ‘File’ stamp indicating it had been filed with the government.
- Statement of Information. In particular the bank needed to know who owned the company. There might be other ways to demonstrate this but a statement of information is probably the easiest way.
- An Employer Identification Number (EIN) from the IRS.
- Two forms of identification for each person. Viktor previously had an account with Washington Mutual, so a single form of identification was sufficient there. I had to provide two pieces. This turned out to be easy: a primary id, my driver’s license, and a secondary id: a credit card with my name on it.
- A checkbook to make the initial deposit/pay fees.
All in all it wasn’t too bad. Apparently we can expect checks and a debit card to arrive within a few weeks. The terms for the account weren’t bad either. Free checks, free debit-cards, no minimum balance and no charges for deposits or withdrawals. That’s pretty much all we need at this point.
Author: Alexander Ljungberg Tags: startup,
WireLoad

A couple of months ago we wrote that Google’s Searchmash was secretly experimenting with the real next thing in search. Today I noticed that a service similar to what I described in that article has already popped up: Yoople. Here’s what they write:
At Yoople! Project we believe that Web Searches are quite good, but not as smart as a human brain could do. As today we are forced to accept the order given by search engines and click the results as they are, unfortunately this does not mean the human searcher agrees with the returned results index. Moreover clicking a result does not mean the website contains the contents we were looking for.
This is essentially true. No matter how good a machine is at sorting search results and removing spam, it will always be just a machine. It cannot possibly know what people wish should be their top result without in some way actually asking the user. Google tries to work around this limitation by assuming that web pages linking to other web pages constitute ‘the people’s voice’ so to speak and that a link to a web page within a certain category is a vote for bringing that page up to the top of search results for that particular category. This is a sensible approach but it is not perfect. A limited amount of links is one problem. It is also not necessarily the case that the most relevant page has the most links to it: consider spam sites or sites that just get a lot of links in general and therefore rank better even for irrelevant searches.
The people voting ranking algorithm does have a couple of flaws though. Once again the most important one is spam. First of all it’s hard to verify that users are humans. If a user had to fill out a captcha thing every single time they want to rearrange some search results it would get old really quickly. And what’s worse: even if there was a good way to verify that the voter really was a human, how would you be able to verify his intentions? Maybe he’s just a guy paid to vote up search results by some company. Imagine Paypal asking their telemarketing section to take a day off their schedule just to go and vote away Paypal Sucks from the major search engines. It wouldn’t cost them much and it’d almost certainly succeed. A great investment of their money and time.
It is not unlikely that this is something we will see more and more off. Realizing the immense power of sites like Digg, marketing companies will start paying little groups of people to get articles on the front page. Imagine if you’re a technology company and you’d normally pay 15 cents per visitor through normal banner advertising or what have you. You could instead give 50 people $10 each and get 15,000 visitors from Digg. It’s cheaper and comes with all the attached buzz. As we move towards people controlled search engines this will definitely become a problem there too: 50 people voting a website up to the top will have a huge impact for most search terms since it is unlikely that most legitimate users will vote at all.
None the less, the way forward is to allow people to reorder their results and to delete spam results. It’s the only way to really teach search engines what us humans actually want. There are problems along the way but there will be solutions.
Author: Alexander Ljungberg Tags: internet
Comments Off
Category:
Other
In a recent writeup, BBC News covers a study by Lancaster University’s Professor Tony McEnery. It was also covered by Ars Technica, who put some attention grabbing spin on it by titling their article “Are iPods shrinking the British vocabulary?”
What the quoted study claims is that an excessive focus on technology is turning teenagers into passive listeners without ability to express themselves in spoken language.
Playing With Wire are today publishing an even more shocking study: both BBC News and Ars Technica are going down the same path as these teenagers. A word analysis of the BBC News article cited above reveals that a full 16% of the words in the article are common words such as ‘of’ and ‘in’.
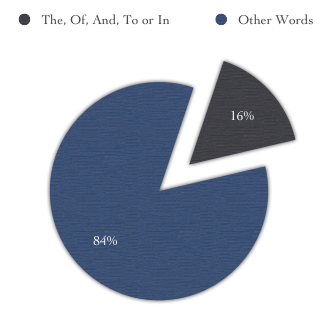
Break-down of the words used in the BBC article. The most common words are used 68 times in an article of only 419 words.
The Ars Technica article also fails to impress in the vocabulary department. 54 of the 301 words in the article are extremely common and simple words. Just like in the BBC News article, the word ‘of’ is used to express a large part of the content.
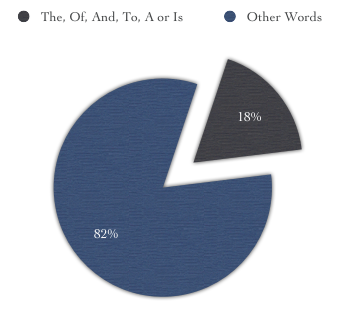
Break-down of the words used in the Ars Technica article. Very common words are used 54 times in this short 301 word article.
Our analysis here at Playing With Wire indicates that since both the Ars Technica and the BBC News articles are published online, there is an excessive reliance on technology. An almost machine like approach to creating articles results in this bleak lack of imaginative word usage.
We absolutely do not think unification of the English language occurs online to reach the widest possible audience. In fact this ubiquitous unsophisticated locution employment has us flabbergasted. It’s stupefying.
Author: Alexander Ljungberg Tags: analysis

This article is going to teach you how to get out the big guns against information theft on your Apple OS X machine. ‘But,’ you say, ‘I don’t have secrets and besides no-one cares about my stuff.’ Think again! If you are a normal computer user it doesn’t take long before you have plenty of very interesting information on your laptop, digitized and ready to be stolen in seconds.

My secret politically sensitive picture – out in the open and ready to be stolen.
- Your website passwords
- Those handy digital bank statements
- Your accounting information
- That picture from the office when you were really drunk
- Your other girlfriend’s or boyfriend’s phone number
Then think about how quickly someone can make a complete copy of all that data: it can take seconds or minutes. And what’s worse, once the cat is out of the bag, it’s likely you won’t manage to get it back in because it will be plastered over half of internet and stored in a database before you know it. We live in the beginning of the information age and information theft is real, fast, and internet enabled.
If you use Safari, most of your passwords are already protected within your Apple Keychain. This guide is about how to protect the rest of your stuff using encrypted disk images. An encrypted disk image is basically a protected folder which you can store on your computer. If you haven’t heard of it yet, encryption is a method to warp data so it can’t be recognized without doing the same process again backwards. In OS X 10.4, this encryption is not toy encryption either. The standard used, AES-128, is the encryption used for ‘SECRET’ level classified information of the American government.
It is all rather simple; just keep in mind that these tips have been written for OS X Tiger (version 10.4) and that things might be a bit different if you have a different version of OS X.
 Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.
Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.- Click the ‘New Image’ button in the upper left part of the main window, or go to File>New>Blank Disk Image in the menus.
- Type in a nice name for your new disk image. I’m going to call mine ‘My Eyes Only’. I’m also going to make it 40MB big by selecting that from the size drop down.
- Set Encryption to ‘AES-128′. Don’t forget to do this or you’re not protecting your data at all!
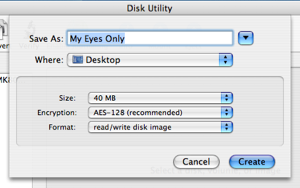
- Click create. You will be asked for a password. Make sure you enter something that you won’t forget, because else your data will be gone forever. No-one will be able to get your data out if the password is lost.
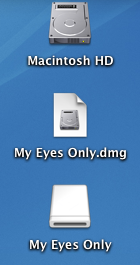 Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.
Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.- Once you are done putting files into your encrypted drive, you will need to eject it.
That’s all. Everything you put into your encrypted drive, ‘My Eyes Only’ in this example, will be encrypted with industry standard encryption. Without your password (which you made really sure to memorize and keep safe) it would take thousands of years for a modern day computer to unscramble your data. I’m just going to go ahead and move my Secret.JPG file into My Eyes Only. Here it is in the safety of 128 bit encryption: 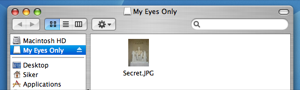
Once I eject this disk the data will be safe and I can rest assured that my picture is a little bit more safe from prying eyes.
Author: Alexander Ljungberg Tags: guide,
Mac OS X,
security
Comments Off
Category: Uncategorized
I know I know. By now you are like, ‘what, another new Cuzimatter feature? Oh my God I don’t know how much more fantastic web 2.0 utility goodness I can take!’
But we had to do it for ourselves. Cuzimatter has been fixed up to generate W3C compatible links. As a bonus we added an ‘icon only’ mode in the advanced settings which we’re going to start using ourselves since our blog writing space is so narrow. Enjoy!
Author: Alexander Ljungberg Tags: Cuzimatter,
internet,
social bookmarking










 My secret politically sensitive picture – out in the open and ready to be stolen.
My secret politically sensitive picture – out in the open and ready to be stolen.

 Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.
Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.