This article is going to teach you how to get out the big guns against information theft on your Apple OS X machine. ‘But,’ you say, ‘I don’t have secrets and besides no-one cares about my stuff.’ Think again! If you are a normal computer user it doesn’t take long before you have plenty of very interesting information on your laptop, digitized and ready to be stolen in seconds.
 My secret politically sensitive picture – out in the open and ready to be stolen.
My secret politically sensitive picture – out in the open and ready to be stolen.- Your website passwords
- Those handy digital bank statements
- Your accounting information
- That picture from the office when you were really drunk
- Your other girlfriend’s or boyfriend’s phone number
Then think about how quickly someone can make a complete copy of all that data: it can take seconds or minutes. And what’s worse, once the cat is out of the bag, it’s likely you won’t manage to get it back in because it will be plastered over half of internet and stored in a database before you know it. We live in the beginning of the information age and information theft is real, fast, and internet enabled.
If you use Safari, most of your passwords are already protected within your Apple Keychain. This guide is about how to protect the rest of your stuff using encrypted disk images. An encrypted disk image is basically a protected folder which you can store on your computer. If you haven’t heard of it yet, encryption is a method to warp data so it can’t be recognized without doing the same process again backwards. In OS X 10.4, this encryption is not toy encryption either. The standard used, AES-128, is the encryption used for ‘SECRET’ level classified information of the American government.
It is all rather simple; just keep in mind that these tips have been written for OS X Tiger (version 10.4) and that things might be a bit different if you have a different version of OS X.
 Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.
Open up Disk Utility. Normally I’d just spotlight ‘Disk Utility’ – like in the picture on the right – but if you need to find it the old fashioned way, look in Applications/Utilities.- Click the ‘New Image’ button in the upper left part of the main window, or go to File>New>Blank Disk Image in the menus.
- Type in a nice name for your new disk image. I’m going to call mine ‘My Eyes Only’. I’m also going to make it 40MB big by selecting that from the size drop down.
- Set Encryption to ‘AES-128′. Don’t forget to do this or you’re not protecting your data at all!
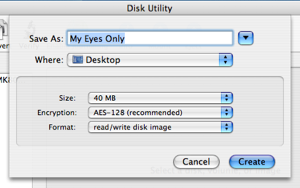
- Click create. You will be asked for a password. Make sure you enter something that you won’t forget, because else your data will be gone forever. No-one will be able to get your data out if the password is lost.
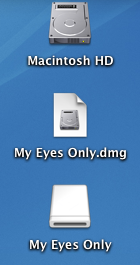 Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.
Your image will be created. You can close Disk Utility once it’s done. Now, you will have an image file ‘My Eyes Only.dmg’, which if you double click and enter your password, will open up as an extra ‘drive’ on your desktop. Disk Utility will open it for you automatically the first time.- Once you are done putting files into your encrypted drive, you will need to eject it.
That’s all. Everything you put into your encrypted drive, ‘My Eyes Only’ in this example, will be encrypted with industry standard encryption. Without your password (which you made really sure to memorize and keep safe) it would take thousands of years for a modern day computer to unscramble your data. I’m just going to go ahead and move my Secret.JPG file into My Eyes Only. Here it is in the safety of 128 bit encryption: 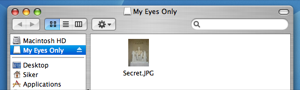
Once I eject this disk the data will be safe and I can rest assured that my picture is a little bit more safe from prying eyes.